Security versus compliance go hand in hand from the multifold perspectives of enterprise defense against much-known ‘risk’. It’s not about the present, cybersecurity has been a priority of business owners ever since the paradigm shift to a secure environment became a necessity to block suspected threats & breaches.
In regards to our topic, both security & compliance are somehow correlated but not exactly the same. Even most tech experts confuse their sense to differentiate between security vs compliance.
If you’re also dilemmatic about security and compliance then this article is for you. Let’s throw some light on the real meaning of both the terms to better understand their differences in technical terms.
What is security in IT?
The basic definition of IT security is framed as a practice of implementing highly effective & powerful control to safeguard a company’s assets & data from unauthorized access.
Security professionals apply the best practices to secure their IT systems, particularly within their business infrastructure & at the enterprise level.
In the context of our discussion on security vs compliance definitions, we would like to outline some important IT security benefits as listed below:
- Restriction of attackers from destructing the company’s data & IT infrastructure.
- Control the amount of damage occurred in case of successful cyber attacks.
- Due diligence to protect & care for confidentiality & security of critical business assets & data.
- More exposure to both architectural & infrastructural components of cybersecurity, testing, & of course information security.
No surprise, there are still many pros to mention about IT security. There was a time when business administrators used to go ahead with technical approaches & count on systems, devices, or tools to secure their network. But today, the scenario is completely different.
Information security or InfoSec revolves around three principles of protecting your business assets, which is also known as the CIA triad.
Taking these three functions of IT security which are confidentiality, availability, & integrity in mind, businesses can freely achieve physical, technical & administrative controls to meet their objectives.
Now let’s define each of these protocols to know how InfoSec implements & manages each of them.
- Confidentiality: It’s about the company’s critical, confidential, & sensitive information related to–customer data, proprietary & profits information, & innovations in the work operations.
The role of IT security is centered on securing this information. By ensuring that only the verified and authorized user(s) and system(s) can access, modify, and use data, businesses can boost their IT security to the next level.
- Integrity: All the data & information it composes must be accurate. In technology terms, integrity is about storing correct information and the system used for it has measures to ensure that.
- Accessibility: The availability of systems & data required to be accessed anytime must be ensured. If a system isn’t accessible, it’s of no use at all!
Stats stating the present state of IT security
Gone are those days when security professionals used to depend on devices like firewalls & content filters along with traditional techniques of network segmentation & access denial. At present times, modern anti-theft agents have become more trained & competent against cybercrimes & security breaches. Today’s IT officers have got various advanced tools & techniques that are quite complex but proactively dominant over hackers.
Here are some interesting stats & facts on IT security:
- 95% of cyber-security breaches happen due to human errors.
- 45% of cyber threats arise from hacking done by technically adept individuals attempting to break vendor-created backdoors or access remote code.
- Security professionals are most likely to use a fuller kit of tools to battle against hackers & their malicious attempts.
- IBM says that it takes 280 days to identify & contain a suspected cyberattack that can cost around $3.86 million on an average.
- Out of 15 billion credentials from over 100,000 data breaches on the dark web, only 5 billion were found unique.
- Businesses suffered 50% more cyberattack attempts in 2021, the most targeted industries were the education/research sector, communications, healthcare, ISP/MSP, & government.
- Cybercriminals can exploit the IT systems of more than 93 % of global companies.
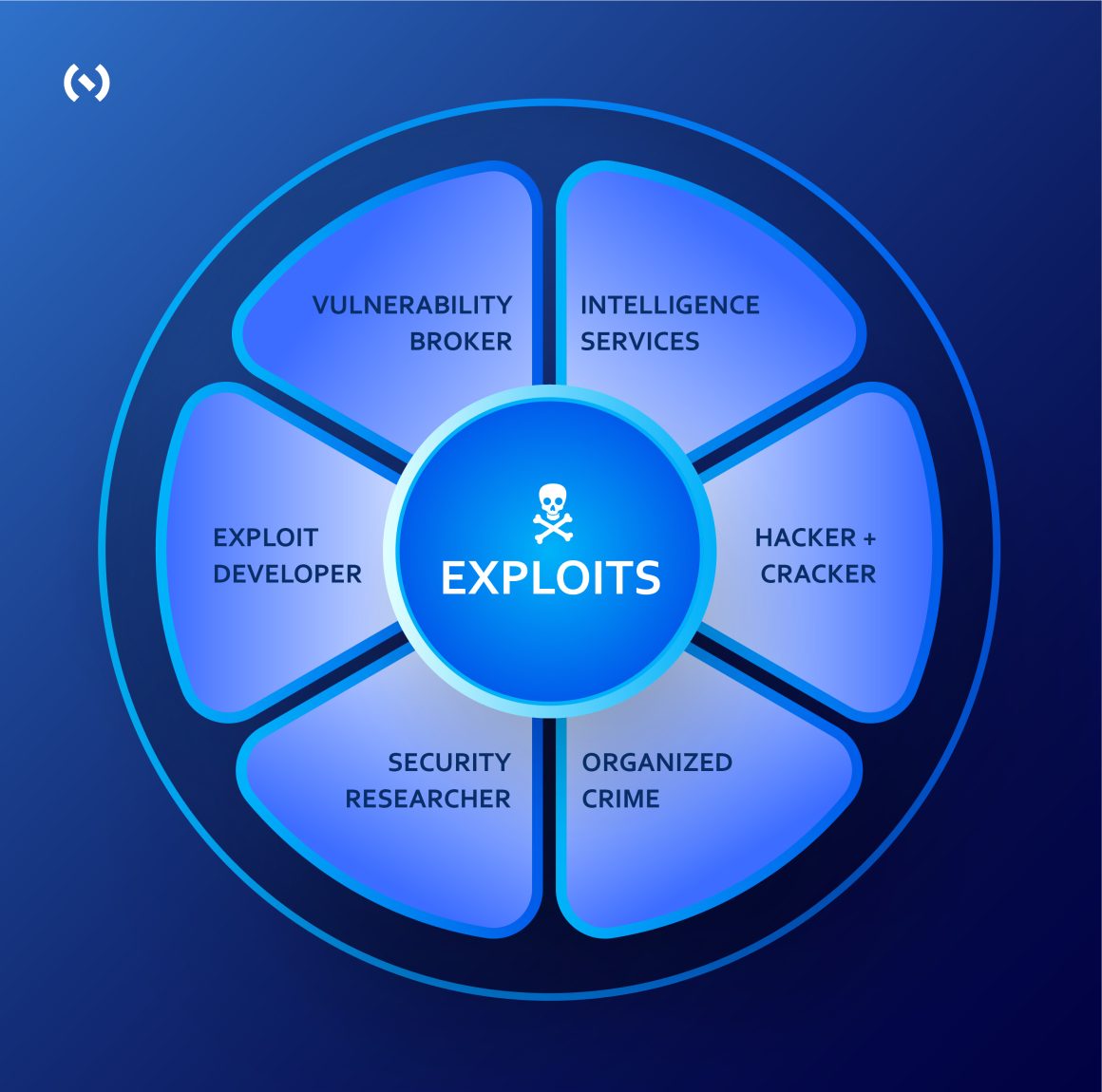
Well, the alarming rise in the number of cyberattacks raised concerns about the enhancement of existing cybersecurity systems. But do you know that besides IT security expenses, about 50% of organizations spend around 6-7% of their revenues on compliance?
Let’s find out why.
And what is compliance in IT?
The meaning of compliance in IT is defined as the process of meeting a third party’s requirements relating to security & related facilities with the aim of running business operations in a particular market or adhering to laws or even with a particular customer.
Compliance may overlap with security—but the intent behind using compliance is totally different. It’s focused on the grounds of third party requirements, such as:
- Industry regulations
- Government policies
- Security frameworks
- Client/customer contractual terms
Let’s say that IT security is a carrot. it motivates the company to protect itself because it is good for the company. IT Compliance, then, is the stick—failure to effectively follow compliance regulations can have serious effects on your business.
Often, these external rules ensure that a given organization can deal with complex needs. These objectives are critical to success because a lack of compliance will result in:
- At a minimum, a loss of customer trust and damage to your reputation.
- At worst, legal and financial ramifications could result in your organization paying hefty fees or being blocked from working in a certain geography or market.
- Areas where compliance is a key business concern:
- Countries with data/privacy laws like GDPR, the California Consumer Privacy Act, and more
- Markets with heavy regulations, such as healthcare or finance
- Clients with high confidentiality standards
These areas almost always demand a high level of compliance. Importantly, IT compliance can apply in domains other than IT security. Complying with contract terms, for example, might be about how available or reliable your services are, not only if they’re secure.
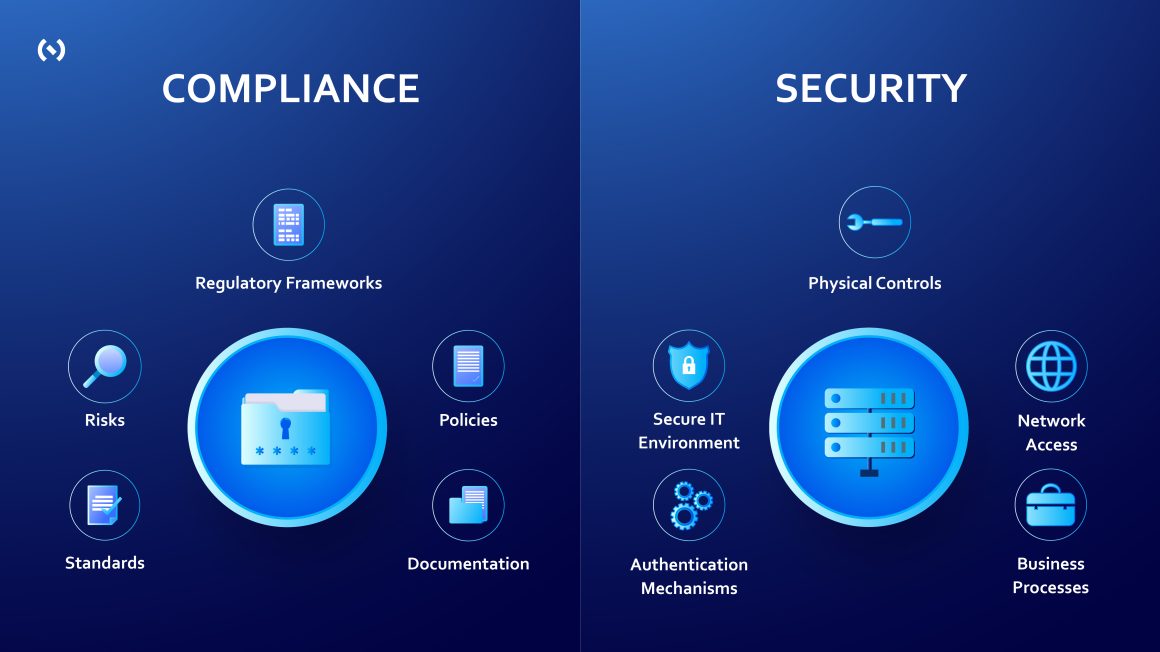
Compliance and Security-Based on Specific Frameworks
Compliance studies a company’s security processes. It details their security at a single moment in time and compares it to a specific set of regulatory requirements. These requirements come in the form of legislation, industry regulations, or standards created from best practices.
Specifically, compliance frameworks include:
1. HIPAA
HIPAA (Health Insurance Portability and Accountability Act) applies to companies in the Health Insurance industry. It legislates how companies should handle and secure patients’ personal medical information. HIPAA compliance requires companies who manage this kind of information, to do so safely. The act has five sections, which it calls Titles. Title 2 is the section that applies to information privacy and security.
Initially, HIPAA aimed to standardize how the health insurance industry processed and shared data. It has now added provisions to manage electronic breaches of this information as well.
2. SOX
The Sarbanes-Oxley Act (also called SOX) applies to the corporate care and maintenance of the financial data of public companies. It also outlines controls for the destruction, falsification, and alteration of data.
SOX attempts to improve corporate responsibility and add culpability. The act states that upper management has to certify the accuracy of their data.
All public companies must comply with SOX and its requirements for financial reporting. Classifying data correctly, storing it safely, and finding it quickly are critical elements of its framework.
3. PCI DSS
PCI DSS compliance is the Payment Card Industry Data Security Standard created by a group of companies who wanted to standardize how they guarded consumers’ financial information.
Requirements that are part of the standard are:
- A secured network
- Protected user data
- Strong access controls and management
- Network tests
- Regular reviews of Information Security Policies
There are four levels of compliance within the standard. The number of transactions a company completes every year determines what level it must comply with.
4. SOC Reports
SOC Reports are Service Organization Control Reports that deal with managing financial or personal information at a company. There are three different SOC Reports. SOC 1 and SOC 2 are different types with SOC 1 applying to financial information controls, while SOC 2 compliance and certification covers personal user information. SOC 3 Reports are publicly accessible, so they do not include confidential information about the company. These reports apply for a specific period, and new reports consider any earlier findings.
The American Institute for Chartered Public Accountants (AICPA) defined them as part of SSAE 18.
5. ISO 27000 Family
The ISO 27000 family of standards outlines minimum requirements for securing information. As part of the International Organization for Standardization’s body of standards, it determines the way the industry develops Information Security Management Systems (ISMS).
Compliance comes in the form of a certificate. More than a dozen different standards make up the ISO 27000 family.

Final words
In layman’s terms, security is practiced for the sake of own’s benefits but compliance is only performed for fulfilling the needs of third-party businesses or a client expecting a secure environment to work together.
The never-ending debate on security vs compliance won’t be ending soon as not all business professionals were familiar with the differences between the two. But yes, we hope this article has dissolved all major misconceptions to differentiate between security & compliance.
Want to secure your business with a robust software solution, Hie HQ is the right technology partner to co-build high-end products with higher chances of success. Our agile methodologies & startup-centric approach are the major USPs of our key service offerings. From ideation to conceptualizing, we strategize to build products two times better & faster.
Apart from security & compliance, we bring our deep expertise in UX/UI design, mobile app development, web app development, backend development, DevOps, 3rd party integrations, & tailored solutions as per your project requirements. Contact us for more information.
FAQs
1. Does compliance overlap with security?
Yes, compliance and security overlap to some extent. Companies that comply with regulations may also have a strong security strategy to protect their data. By being compliant, organizations make themselves more vulnerable to potential fines or legal action from government officials. However, this can also be an opportunity for them to strengthen their security measures by implementing best practices such as whistleblower protections and encryption of sensitive data.
2. What are some of the compliance and security best practices?
When it comes to compliance and security, it is important to follow best practices that are specific to your industry. For example, if you are in the medical field, you should adhere to HIPAA standards. CISPA and other data privacy laws may apply if you work in the technology sector. And finally, PCI Compliance should be of utmost importance if you are a retailer.
By following these guidelines and staying up-to-date on changes in regulations and best practices, you can ensure that your business remains compliant with current legislation and protects valuable personal information from cyber attackers.
